Business leaders need to ensure that they proactively fight battles against ever increasing cyber threats to secure their business while moving along with converged platforms and advancements in technologies . With over one decade of experience in providing Solutions and Services to Telecom Operators, Tata Communications Transformation Services (TCTS) enables your organization to safeguard business assets, to reduce operational costs and to meet compliance requirements with applicable laws and regulations thereby strengthening your organization's security infrastructure with performance-based metrics.
TCTS enables security value chain that involve robust planning, tailored design with multilayered network security with reduced implementation timelines and seamless migration of security solutions.
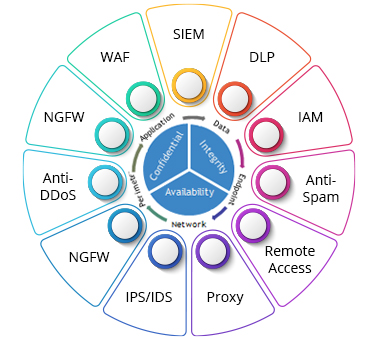
TCTS addresses the security concerns of 4G/5G and safeguard telecom business and its customers and assist to comply with regulatory and Industry standards along with proven security assessments.

TCTS’s approach of managed security utilizes Virtualised Network Functions (VNFs) integrated with SD-WAN and NFV environments such as Universal Customer Premises Equipment (uCPE), NFV Infrastructures (NFVI), and emerging Multi-Access Edge Compute (MEC) environments
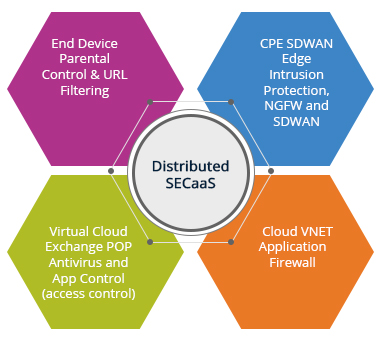
TCTS helps customers to provide solutions to implement end to end security lifecycle management from IoT device sensors till platform gateway.
TCTS’s security managed has comprehensive protection service from cyber threats by reducing ongoing operations costs with guaranteed performance service levels by leveraging proven processes and procedures.

TCTS assist customers to identify security gaps in cloud platforms and thereby provide solutions for securing their cloud workloads using industry best standards and solutions.

TCTS with an experience of Consulting & Transformation would work with you in simplifying security choices based on standards and business vertical-based security consulting & advisory that helps to drive strategy, risk management and compliance.

Our Cyber Assurance services assist to provide key information about the effectiveness of your cybersecurity risk management along with capability and maturity.
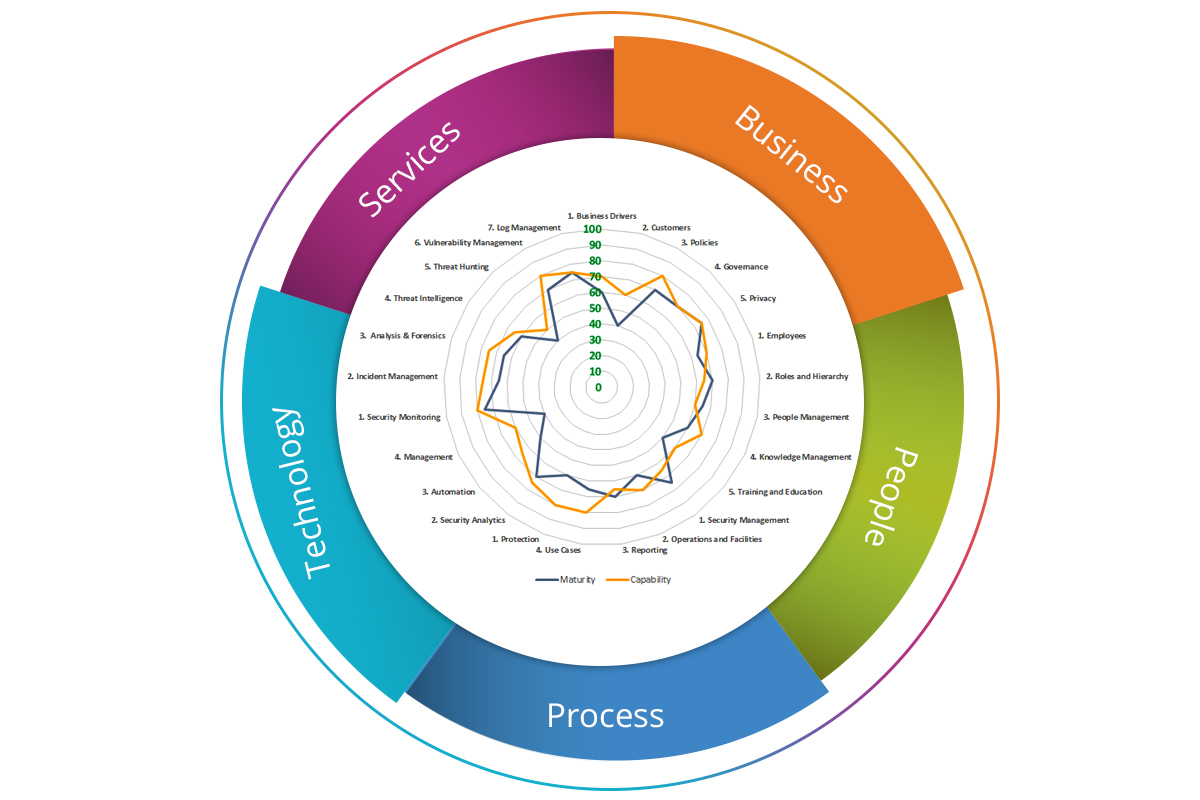
Capabilities that cover the gamut of end-to- end security operations across the IT/ telecommunication landscape.
Dedicated security research lab centres and partnership engines.
Variety of engagement models from consumption models to multiyear transformational projects to enable consistent, low cost and highly efficient delivery.
‘Security integration’ frameworks to transform your organisation from its current-state maturity level to its future desired state.
Range of service delivery models, including on-premise SOC, staff augmentation, offshore monitoring and management, design-build-operate models.
Transformation accelerators and methodologies to mitigate cybersecurity concerns.
Trusted partner for CSPs, helping them to cost-effectively improve their information security processes, meet security best practices and achieve regulatory compliance.