In today’s evolving threat landscape, traditional perimeter-based security models are increasingly inadequate. As digital assets proliferate—fuelled by cloud adoption and remote work—organizations must confront sophisticated risks that demand a fundamentally new approach to cybersecurity. Zero Trust provides a robust framework that dispenses with implicit trust, insisting on continuous verification for every access request regardless of its origin.
Rethinking Security: The Zero Trust Framework
Zero Trust is a strategic cybersecurity model that challenges the long-held assumption of inherent trust within a network. Rather than presuming that internal entities are safe while external ones are suspect, Zero Trust mandates rigorous identity verification for every user and device before granting access to critical resources. This continuous validation significantly limits the potential for lateral movement once a breach occurs.
Traditional vs. Zero Trust Security Models
Traditional security approaches operate under a binary assumption: trust the insiders and distrust the outsiders. This method creates vulnerabilities because a malicious actor who gains internal access can move freely across the network, compromising sensitive data. In contrast, Zero Trust Architecture requires verification for every access attempt—whether from within or outside the organizational perimeter—thus drastically reducing the potential attack surface.
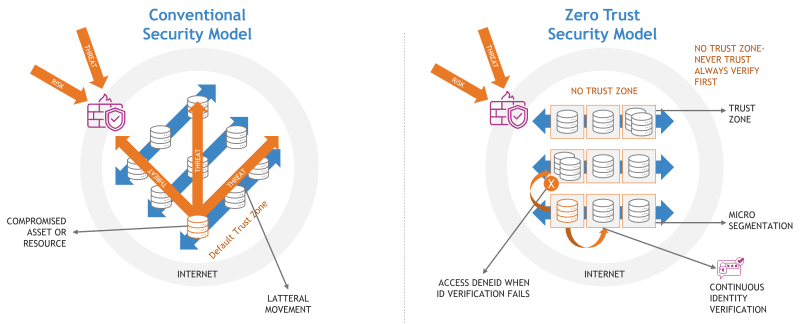
Fig. 1 – Conventional Security Model vs Zero Trust Security Model
Core Principles of Zero Trust Architecture
Implementing a Zero Trust strategy requires adherence to several foundational tenets:
- Resource Identification: Clearly classify data and computing services as distinct resources to facilitate precise access control.
- Secured Communication Across All Locations: Ensure that access requests—regardless of origin—meet the same rigorous security standards.
- Session-Based Access Control: Evaluate the trustworthiness of each access session individually and grant the minimum privileges required to perform specific tasks, with resource-specific authentication and authorization.
- Dynamic Policy Management: Establish adaptive access policies that account for various attributes, including:
- User identity
- Endpoint state (e.g., software version, network location, credential status)
- Behavioural indicators (e.g., device analytics, user behaviour patterns)
- Environmental factors (e.g., network location, time, historical threat data)
- Application condition
- Comprehensive Security Posture Monitoring: Continuously collect and analyze data on asset status and network infrastructure to inform and enhance overall security measures.
- Ongoing Identity Management: Implement processes for periodic reauthentication and reauthorization to ensure that access rights remain appropriate over time.
These policies should be calibrated according to the criticality of each resource.
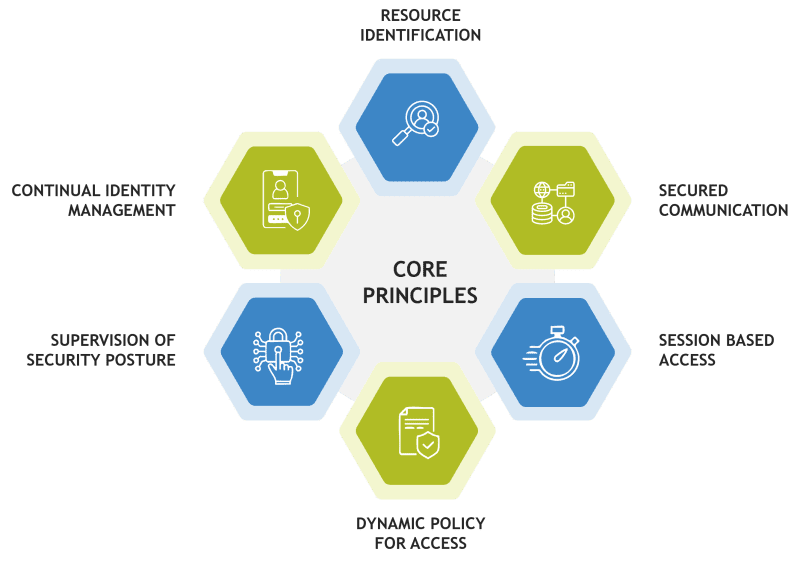
Fig 2 – Tenets of a Zero Trust Strategy
Operationalizing Zero Trust: The Process Flow
In a Zero Trust environment, every access request—from endpoints, applications, or users—is systematically verified against pre-defined policies. Whether these policies are role-based or attribute-based, they function to rigorously assess and validate each request, ensuring that only authenticated and authorized entities gain access to the network.
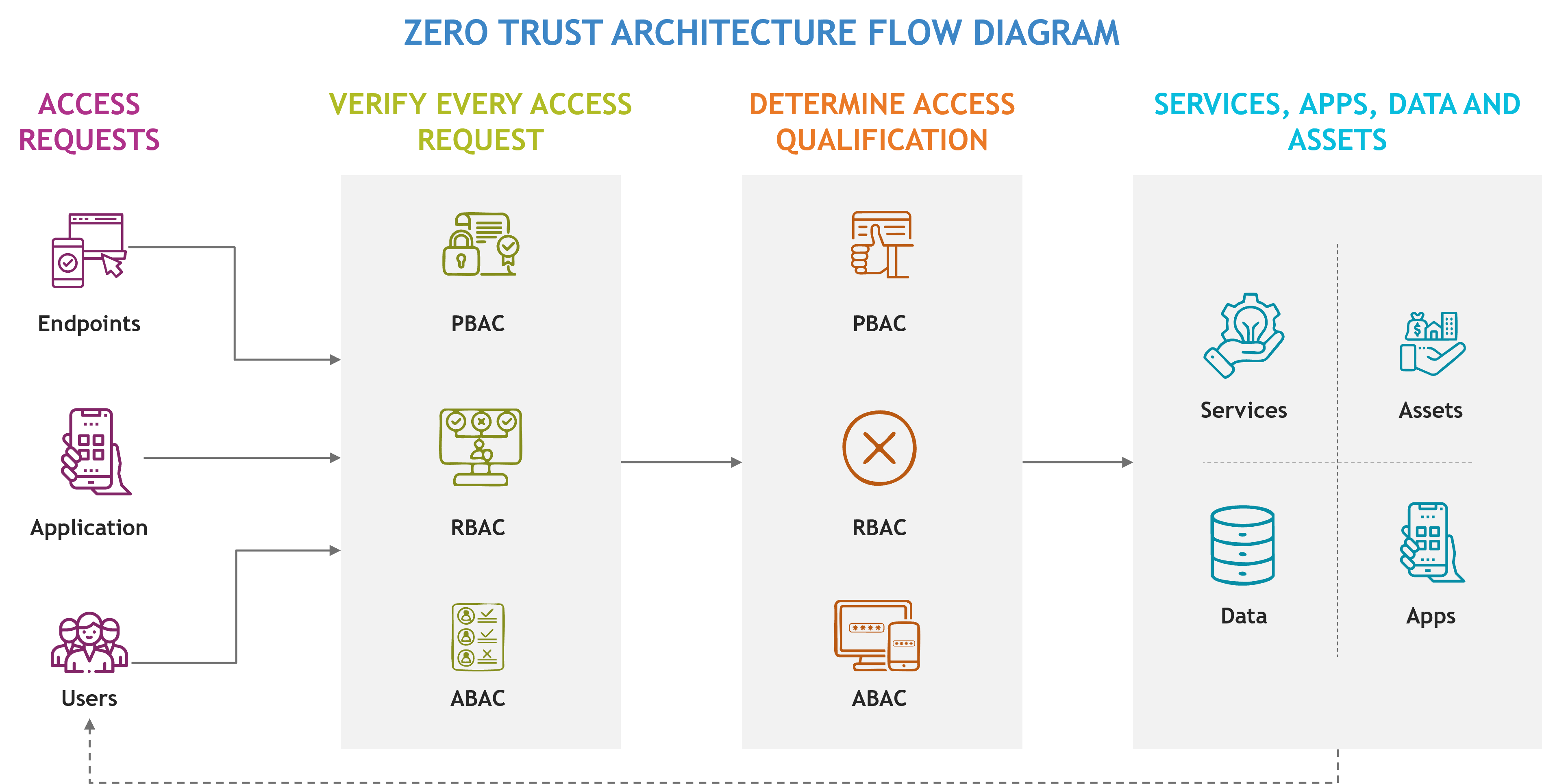
Fig 3 – Zero Trust Architecture Flow Diagram (Source: Ace Cloud Hosting)
Benefits of Zero Trust Framework
Adopting a Zero Trust framework delivers several distinct advantages:
- Enhanced Flexibility: Zero Trust is ideally suited for today’s hybrid and remote work environments, enabling secure access across diverse devices and locations.
- Reduced Attack Vectors: By enforcing the principle of least privilege, Zero Trust minimizes exposure, ensuring that users and devices have access only to the resources necessary for their roles.
- Strengthened Security Posture: Continuous verification dramatically lowers the risk of data breaches and insider threats by ensuring that every access attempt is rigorously authenticated and authorized.
Challenges in Implementing Zero Trust
Transitioning to a Zero Trust model also presents challenges that organizations must navigate:
- Initial Investment and Complexity: Implementing Zero Trust requires significant upfront investment in technologies such as Identity and Access Management (IAM), Multi-Factor Authentication (MFA), and micro-segmentation. The integration of these systems may necessitate specialized personnel or retraining of existing staff.
- Legacy System Constraints: Many organizations rely on legacy systems that are incompatible with Zero Trust principles, requiring substantial upgrades to network infrastructure and applications.
- Configuration Difficulties: Since Zero Trust is not a single-solution framework, integrating and configuring existing tools to enforce the principle of least privilege can be complex and challenging.
Conclusion
Zero Trust Architecture is not a one-time implementation but an evolving process that continuously enhances an organization’s security posture. With strategic investments in technology and the right integration partners, the transition to a Zero Trust framework can be achieved efficiently. Given that insider threats contribute significantly to security incidents, the adoption of Zero Trust represents a critical evolution in safeguarding modern organizations.





















![Telco Cloud: A Key Enabler to Telco Transformation [Part 1]](https://www.tatacommunications-ts.com/wp-content/uploads/2023/06/Telco-Cloud-blog_image-1-500x383.png)